Setting up Rules
Rules allow for the automation of access assignments based on select criteria. These can be used to assist with both ensuring that identities/users have the access they require based on location, job description or a number of other criteria, and also to make sure that access is removed when an identity/user does not require it or changes position or job role.
There are four types of rules that can be configured:
Access Group Rules: Allow for access groups to be assigned based on select criteria
Auto Approve: Automatically approve assigning of access groups to an identity
Credential Suspension: Automatically removes individual card access when inactive by the user for the specified time selected
Use it or Lose it: Automatically removes individual access rights when inactive by the user for the specified time selected
Access Group Rules
To create a new Access Group Rule:
Click the CONNECT tab
In CONNECT, select the Configuration tab
On the Configuration page, click the Rules button
On the Rules page, click the Access Group Rules button
On the Access Group Rules page, click the New button in the upper right corner
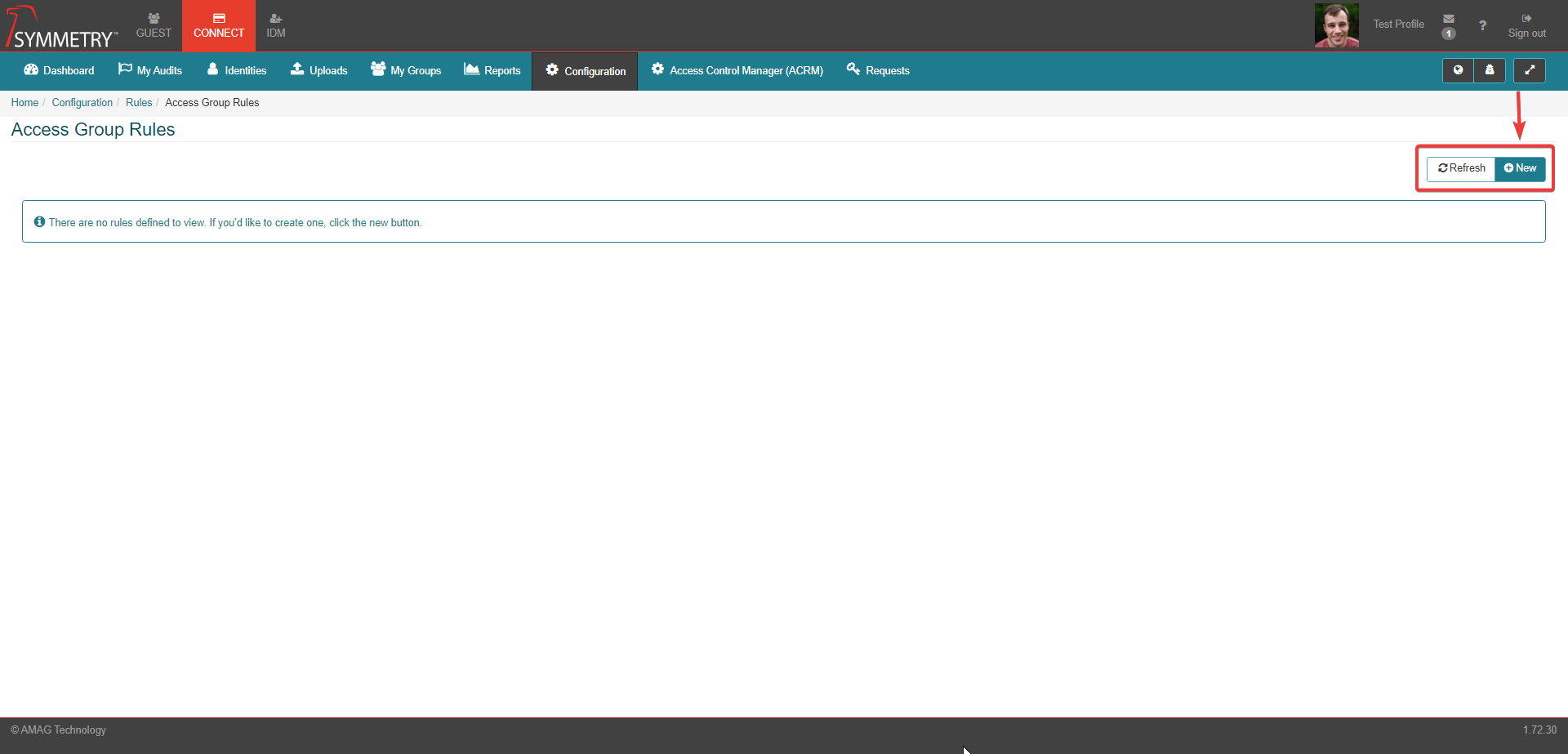
Next enter the following fields:
Name: How the access group rule will be identified
Type: The type of rule being created (see list below for the options)
Add access (access will be granted to Identities who met the criteria of the rule)
Request access (access can only be requested by Identities who met the criteria of the rule)
Approve access (access can only be approved by approvers who met the criteria of the rule)
Access Conditions: The criteria that must be met to get the Access Group(s), selectable attributes include:
Building
Companies
Department
Employee Types
Identity Category
Access Groups
Any User Defined fields configured in CONNECT
Access Groups: For Add Access rules, the access groups that will be assigned if the conditions are met
To create Access Conditions, select the desired attribute and the desired value. You can then select a boolean value. For text attributes, the options are 'equal to' and 'not equal to'. For other attributes, there are extra options: 'less than', 'less than or equal to', 'greater than' and 'greater than or equal to'. Multiple attributes can be applied by selecting the plus icon to the right of the Conditions box. You can also delete one or more attributes by selecting the bin icon.
Click the Submit button
Note
You can see how many identities fit the criteria and will be assigned the access by clicking the Calculate Now button.
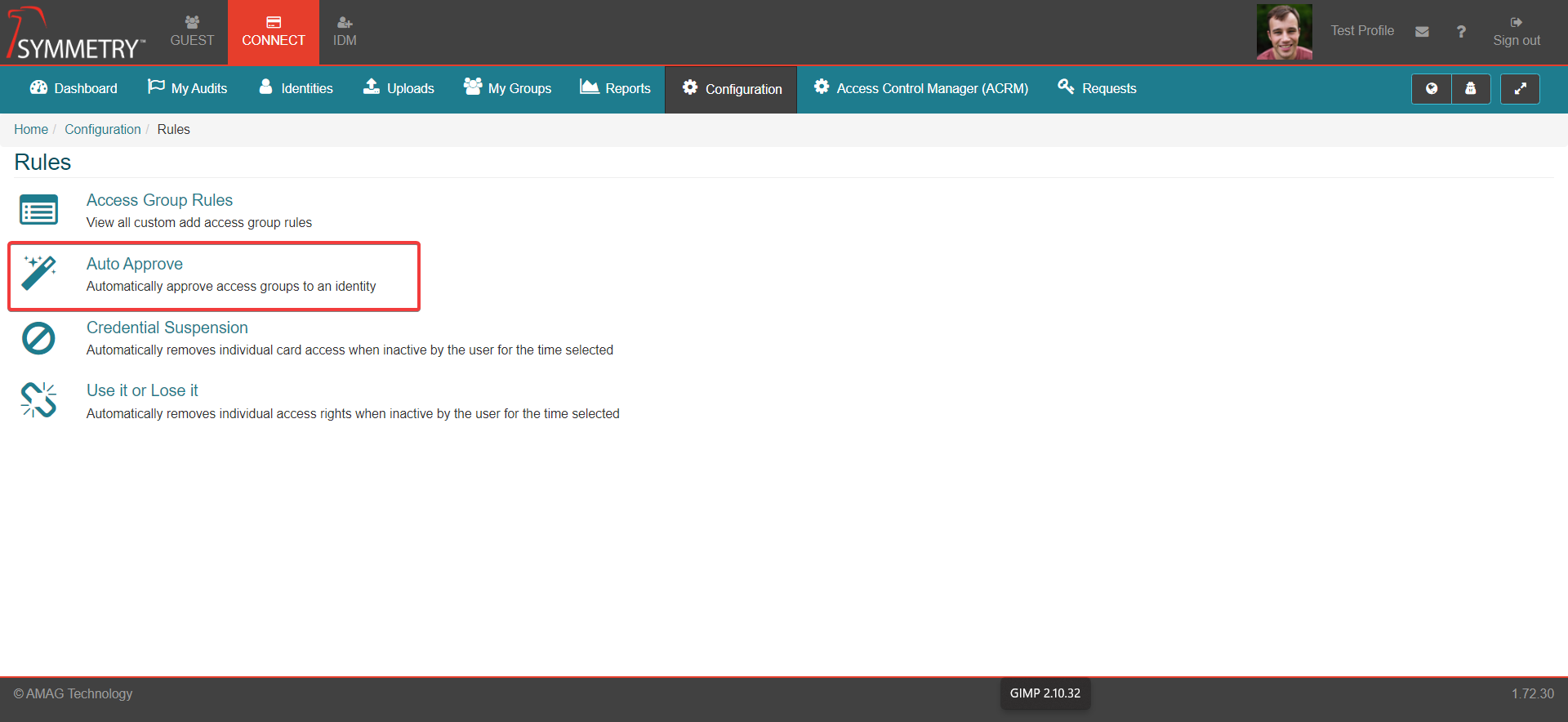
Auto Approve
To setup Auto Approve rules:
Click the CONNECT tab

In CONNECT, select the Configuration tab

On the Configuration page, click the Rules button

On the Rules page, click the Auto Approve button
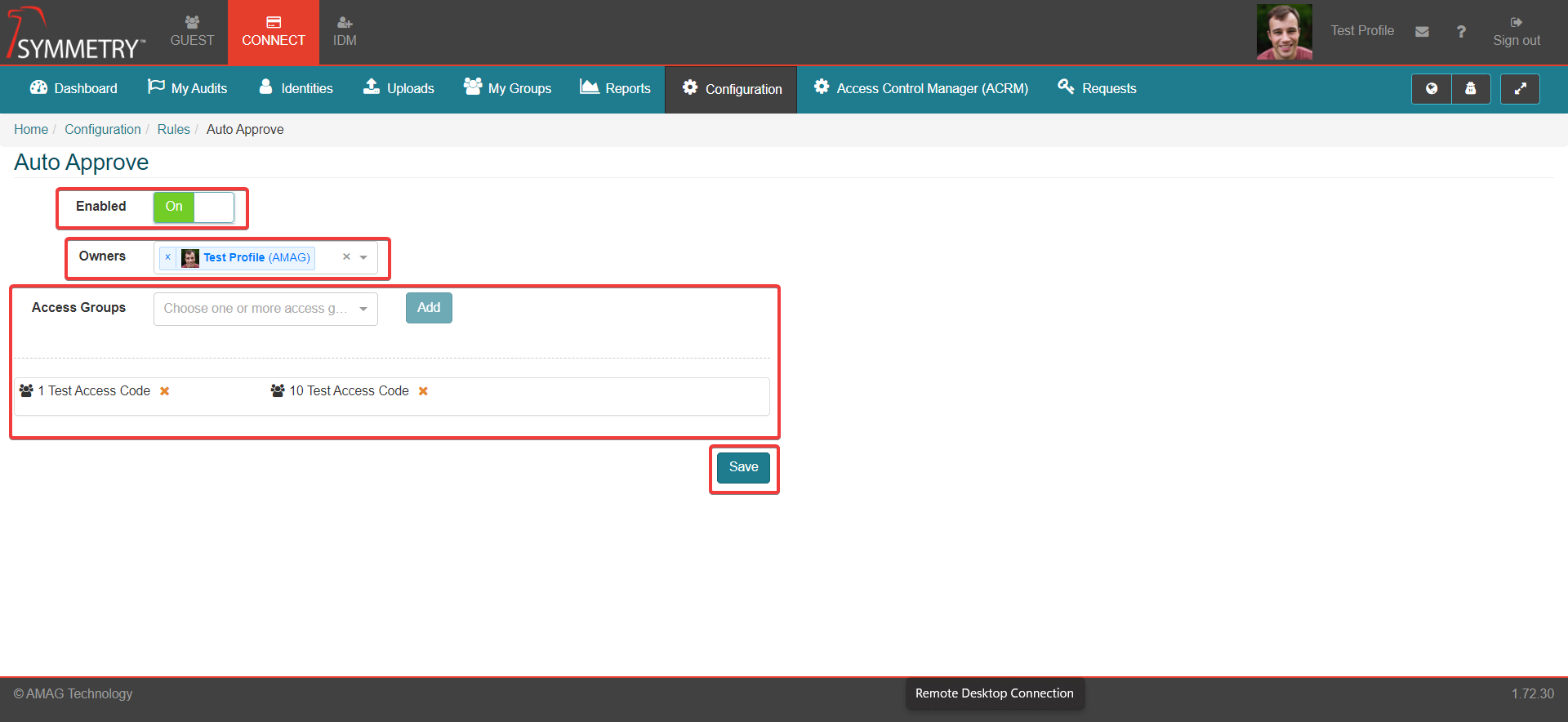
On the Auto Approve page, select the On option next to the Enabled field
Start typing the name of the Identity / User who will own the rule and select them from the resultant dropdown list. Multiple owners can be selected.
Next, start typing the name of the Access Group that should be auto-approved and select it from the resultant dropdown list. Then click the ADD button. Multiple Access Groups can be added to the rule.
Click the Save button to activate the rule.
Credential Suspension
To configure the credential suspension rule:
Click the CONNECT tab

In CONNECT, select the Configuration tab

On the Configuration page, click the Rules button

On the Rules page, click the Credential Suspension button
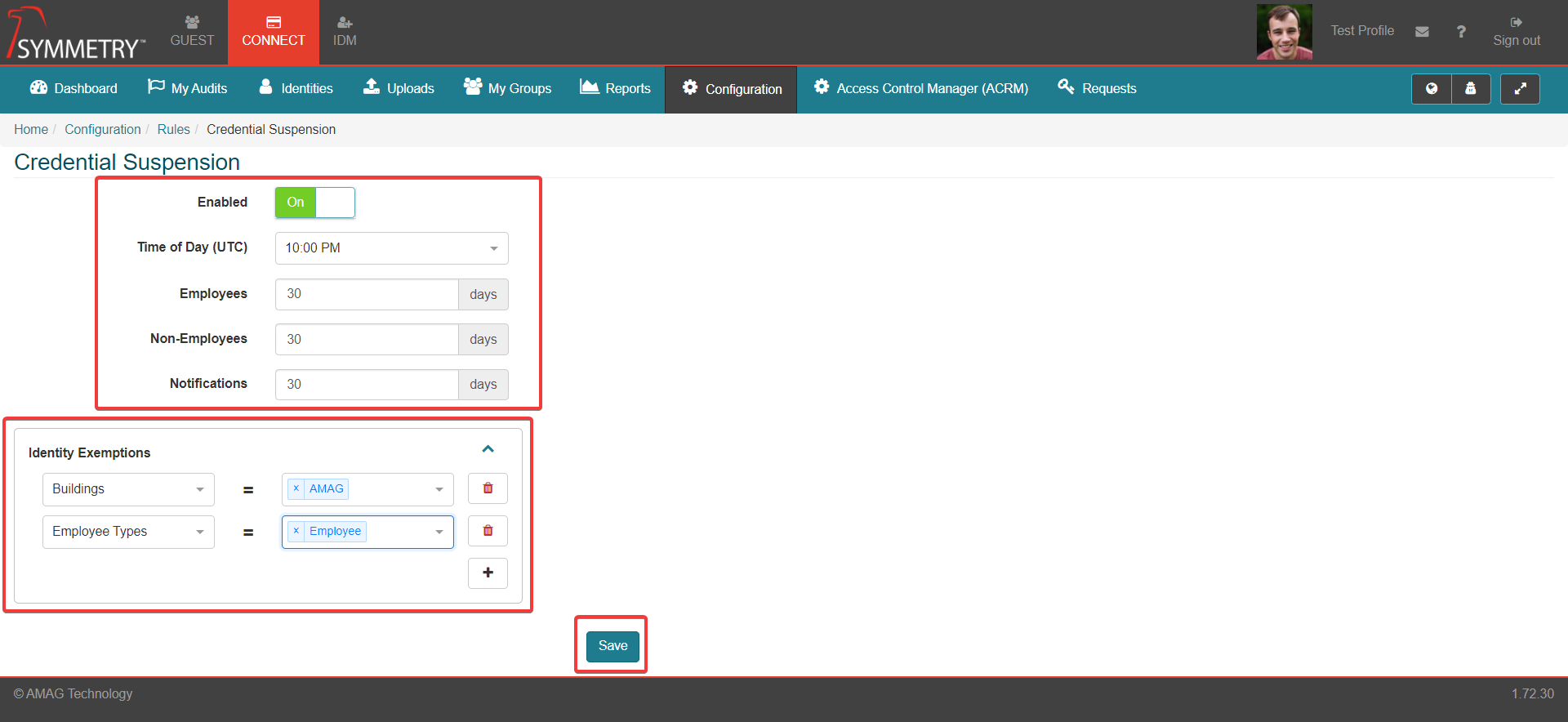
On the Credential Suspension page, select the On option next to the Enabled field
Enter the following fields:
Time of Day (UTC): This is the time of day that the notifications will be sent, in UTC. User can select hourly timestamps from the drop down list.
Employees: The number of consecutive days that a credential can remain inactive before they are suspended. Only for identities that have the Employee identity type.
Non-Employees: The number of consecutive days that a credential can remain inactive before they are suspended. Only for identities that have the Non-Employee identity type.
Notifications: The number of days that a credential can remain inactive before a notification warning is issued. It is recommended that Notifications are sent out a sufficient time before suspension to allow the user to use their card if desired and prevent the suspension.
Identity Exemptions: One or more attributes that if contained in the identity record will make the credential exempt from suspension.
Multiple attributes can be applied, by selecting the additional button

Selectable Attributes include:
Building
Companies
Department
Employee Types
Identity Category
Click the Save button to activate the rule
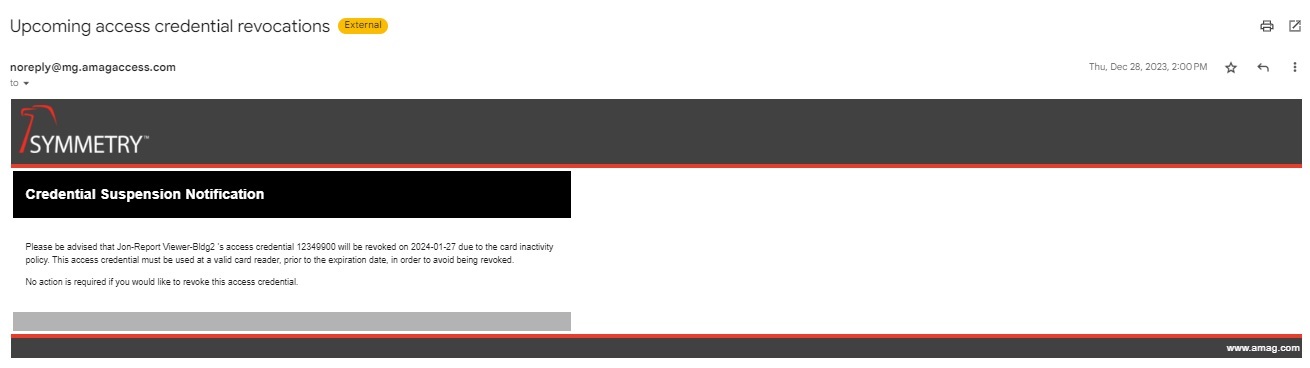
If a credential remains inactive for the length of time configured in the rule for Notifications, a 'Upcoming access credential revocations notification is sent to the affected user configured similarly to the example below.
If a credential remains inactive for the length of time configured in the rule for Employees / Non-Employees, the credential is revoked and removed from the Identity in CONNECT.
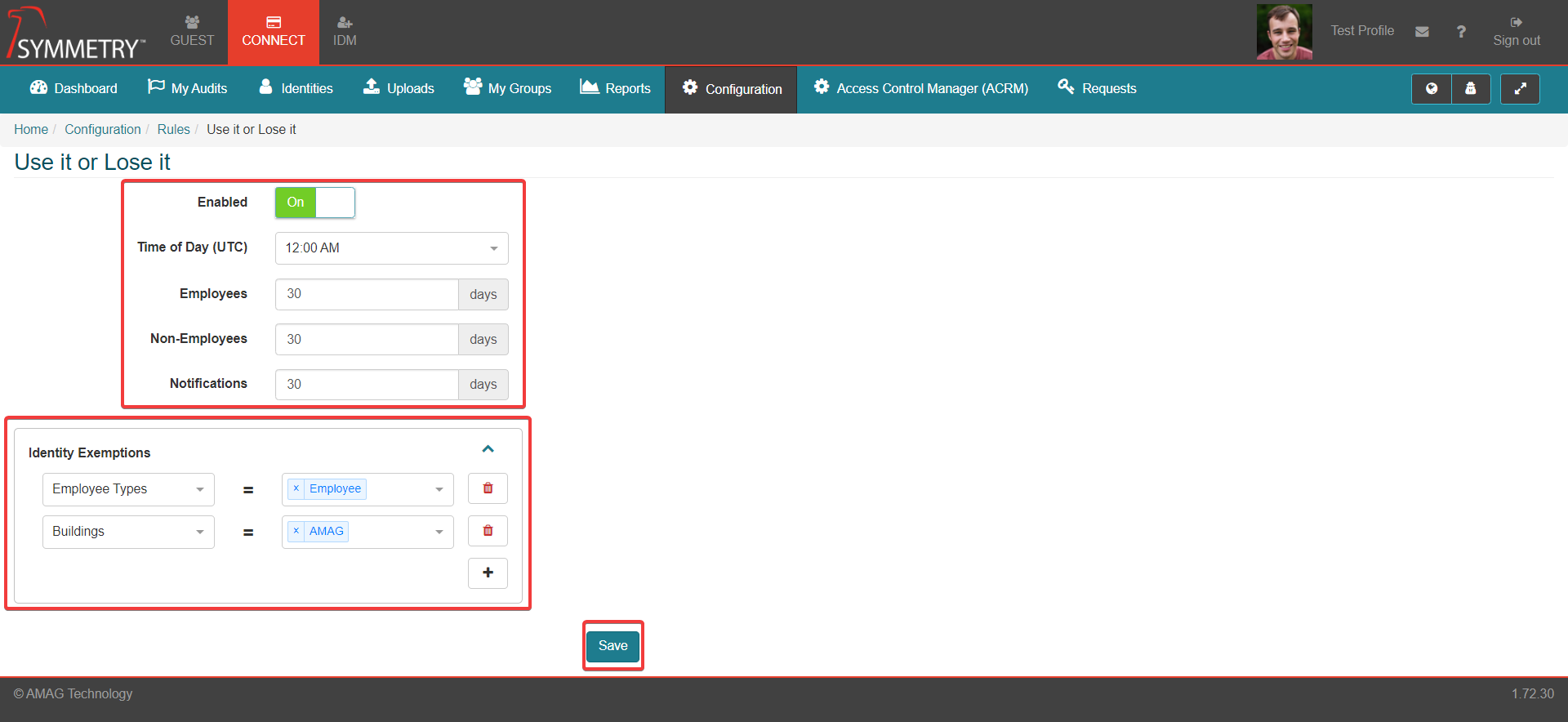
Use it or Lose it
To configure the Use it or Lose it rule:
Click the CONNECT tab

In CONNECT, select the Configuration tab

On the Configuration page, click the Rules button

On the Rules page, click the Use it or Lose it button
On the Use it or Lose it page, select the On option next to the Enabled field
Enter the following fields:
Time of Day (UTC): This is the time of day that the notifications will be sent, in UTC. User can select hourly timestamps from the drop down list.
Employees: The number of consecutive days that a Access Group can remain unused for before it is revoked. Only for identities that have the Employee identity type.
Non-Employees: The number of consecutive days that a Access Group can remain unused for before it is revoked. Only for identities that have the Non-Employee identity type.
Notifications: The number of days that a Access Group can remain unused for before a notification warning is issued. It is recommended that Notifications are sent out a sufficient time before revocation to allow the user to use their Access if desired and prevent the revocation.
Identity Exemptions: One or more attributes that, if contained in the identity record, will make the Access Group exempt from revocation.
Multiple attributes can be applied, by selecting the addition button

Selectable Attributes include:
Building
Companies
Department
Employee Types
Identity Category
Finally, click the Save button to activate the rule.
If a Access Group remains unused by the Identity for the length of time configured in the rule for Notifications, a 'Upcoming access use it or lose it' notification is sent to the affected user. See example in CONNECT Email Templates Access Group Use It or Lose It for further details.