LDAP Configuration
Warning
The LDAP configuration must only be completed by a user with a fundamental understanding of an active directory system and the settings.
Note
This is only available to On-Premise customers.
Note
The LDAP (Lightweight Directory Access Protocol) is supported from IDM version 1.61.0 onwards.
Introduction into the IDM LDAP (Lightweight Directory Access Protocol), Field descriptions and how to access the LDAP configuration screen.
How to Access the LDAP configuration area
Overview and description of each field in the configuration area
How to configure the LDAP settings
How to bypass LDAP
LDAP Configuration Access
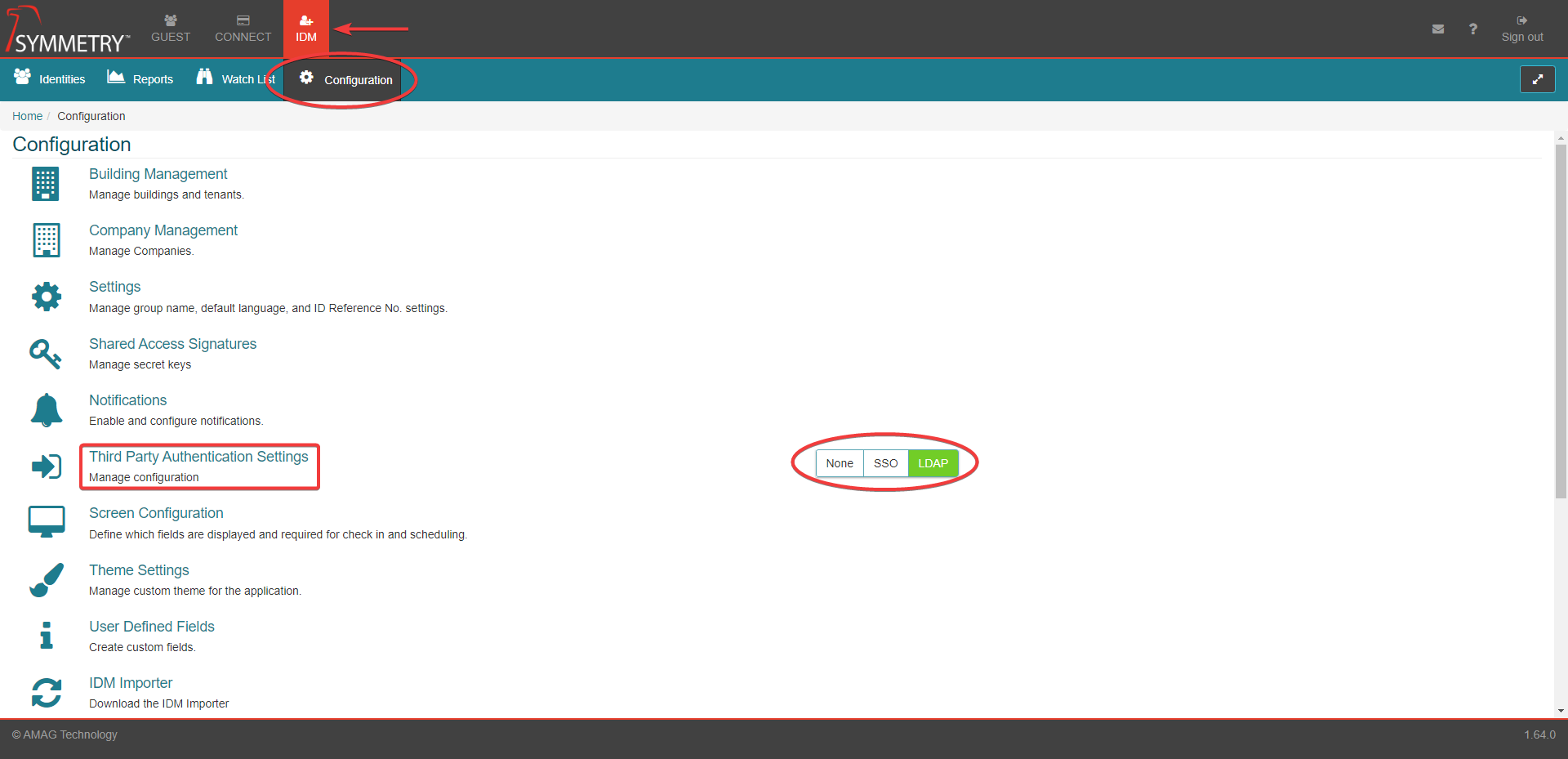
Select the IDM tab at the top of the screen.
Select the Configuration tab.
Select the LDAP option toggle.
Select the Third Party Authentication Settings and enter the LDAP configuration screen.
If changes or updates are to be made to the LDAP settings, scroll down to the bottom of the LDAP configuration screen and select Edit. If no changes are required select Back to exit the configuration screen.
There is the option to test the LDAP configuration settings prior to confirming changes with the Save button.
Select the Test edited LDAP Configuration button.
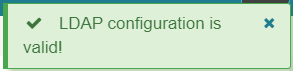
If there are no missing fields or any issues found with the configuration a green box stating LDAP configuration is valid! will be shown on the screen.
If there are missing fields or issues found with the configuration a red box stating the issue or highlighting the missing field will be shown on the screen.
After the completion of any changes or updates made to the LDAP settings select Save to save and apply the changes or updates, or select Cancel to discard any changes or updates made.
LDAP Configuration Screen Descriptions
Note
Required fields are indicated with a red Asterisk.
A brief description of each LDAP configuration screen field.
This information is also available by selecting the Toggle Help icon. 
General:
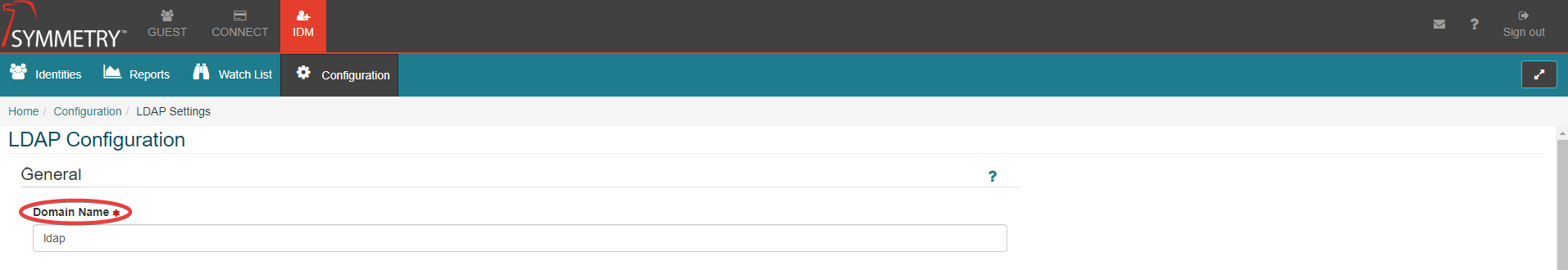
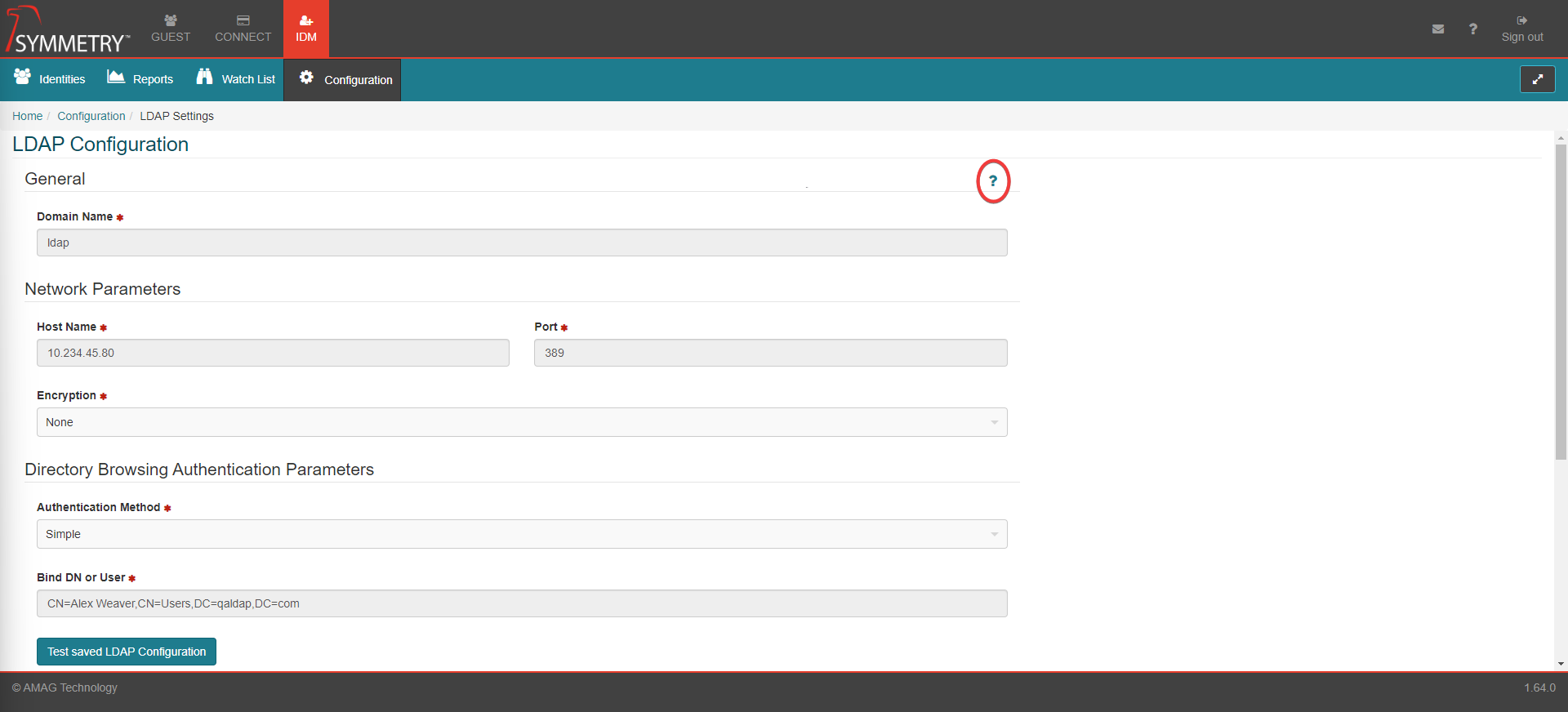
Domain Name: Unique domain name prefix used to login into Symmetry Connect as '<DomainName>\<username>'. For example: 'mydomain', 'mydomain.com', 'mydomain-test'
Network Parameters:
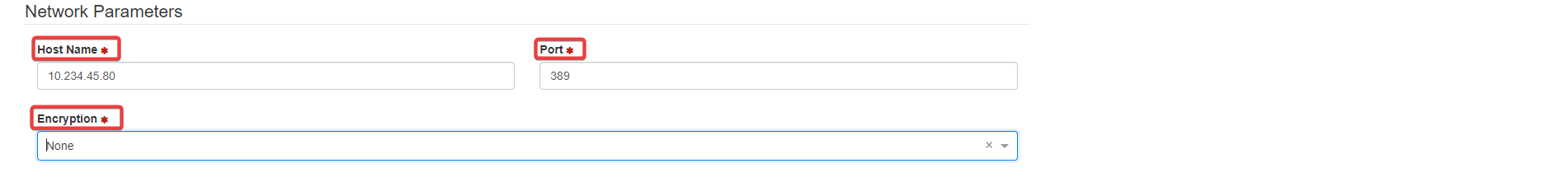
Host Name: Server name or IP address
Port: Server port number. Default is 389 or 636 for SSL.
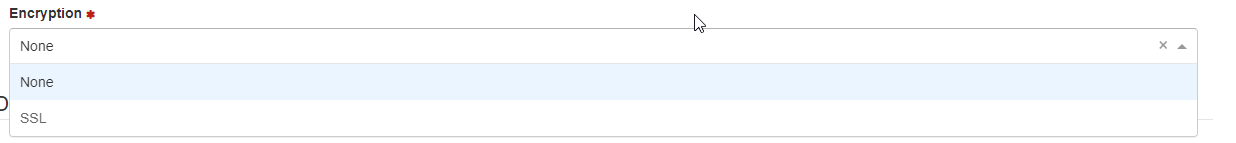
Encryption: Encryption type required by the server
Directory Browsing Authentication Parameters:

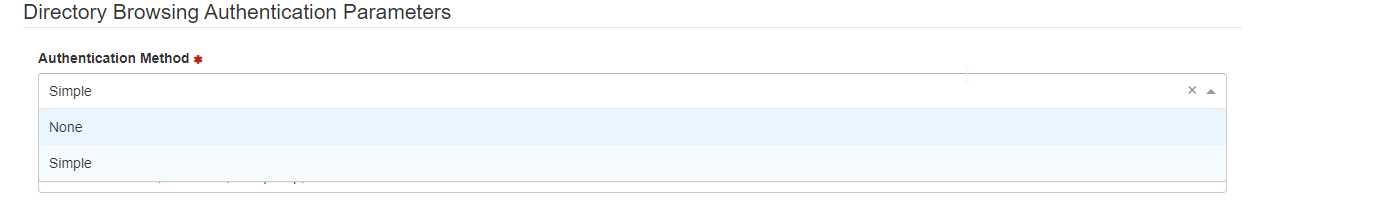
Authentication Method: Authentication method required for searching the user directory
Bind DN or User: Distinguished name or username for the user with read right access to the directory. For example: 'uid=readaccessuser,ou=users,dc=mydomain,dc=com', 'jsmith@mydomain.com', 'mydomain\pbird'
Bind Password: User Password
Test Edited LDAP Configuration: Allows a test of the information to be carried out prior to final save of configuration
User Authentication Parameters:
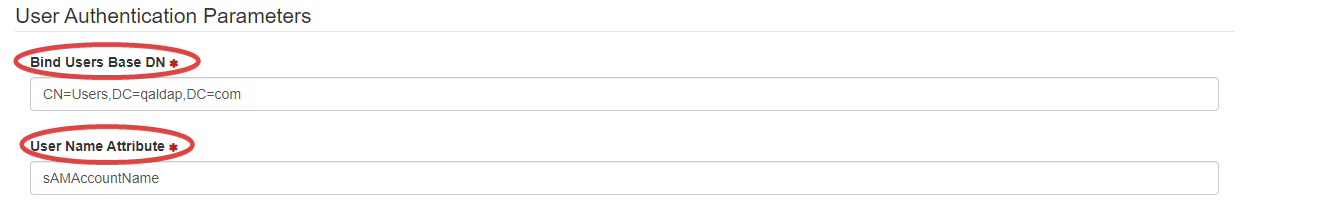
Bind Users Base DN: Users base distinguished name. For example:'ou=users,dc=mydomain,dc=com'
User Name Attribute: Directory user attribute storing username. For example: 'uid', 'sAMAccountName', 'userPrincipalName'
IDM to LDAP Mapping Attributes:
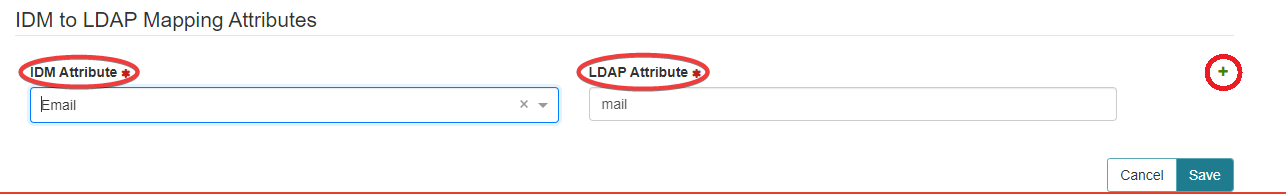
IDM Attribute: Directory user attributes needed in order to match a unique Symmetry Connect identity
LDAP Attribute: Must correlate directly with the IDM attribute
Add a Row:
 Allows an additional row of IDM Attribute and LDAP Attribute fields to be added
Allows an additional row of IDM Attribute and LDAP Attribute fields to be added
LDAP Configuration
Warning
The LDAP configuration must only be completed by a user with a fundamental understanding of an active directory system and the settings.
Warning
It is strongly recommended to set at least one account to Allow LDAP Bypass while configuring LDAP to prevent the risk of being locked out of your account. This can be done via the IDM tab once LDAP has been enabled.
Warning
The user must be a System Administrator to perform the following steps.
Note
Required fields are indicated with a red Asterisk.
Guide to the LDAP (Lightweight Directory Access Protocol) configuration.
Domain Name: Provide the users unique domain name used when logging into Symmetry Connect.

Host Name: Provide the correct server name or IP address that the user wants to connect to.

Port: Provide the port number Symmetry Connect must use for communication with the domain using LDAP, which is used for single-sign on.
The default when SSL encryption is not used is 389.
The default port number when SSL is used is 636.
Encryption: Select either SSL or None.
Symmetry Connect uses SSL Encryption for communications with the global catalog.

Authentication Method: Select the authentication method required for searching the user directory.
Select either Simple or None.

Bind DN or User: Provide a distinguished name or username for a user with the correct read rights to access the user directory.
Bind Password: Provide the users password.

Test Edited LDAP Configuration: Test the configuration settings.
If there are no missing fields or any issues found with the configuration a green box stating LDAP configuration is valid! will be shown on the screen.
If there are missing fields or issues found with the configuration a red box stating the issue or highlighting the missing field will be shown on the screen.
Bind Users Base DN: Provide the users base distinguished name.
User Name Attribute: Provide the directory user attribute storing username.

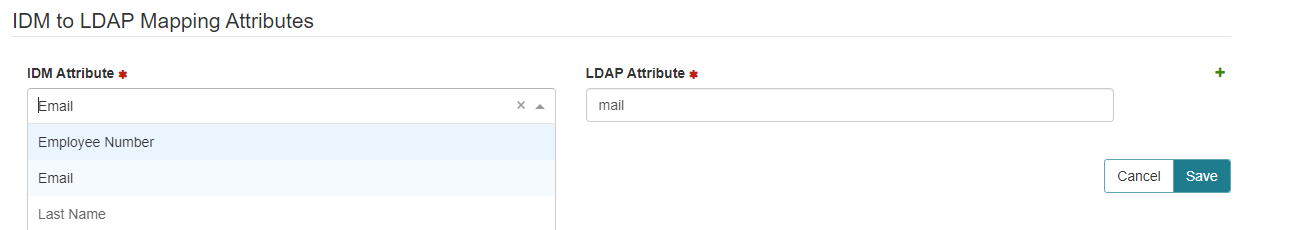
IDM Attribute: Provide the directory users attributes in order to match a unique Symmetry Connect identity. More than 1 attribute can be used by selecting the Add a ROW button.
The user must select at least one IDM attributes, the ability to select several attributes is also supported.
For example:
Email
Employee Number
Last Name

LDAP Attribute: Provide the LDAP attribute that correlates directly with IDM attribute.

After the completion of any changes or updates made to the LDAP settings select Save to save and apply the changes or updates, or select Cancel to discard any changes or updates made.
Bypass LDAP Login
Warning
The user must be a System Administrator to perform the following steps.
Note
Required fields are indicated with a red Asterisk.
The following steps instruct the user how to allow or to bypass third party authentication, this includes LDAP (Lightweight Directory Access Protocol) and SSO (Single Sign-On).
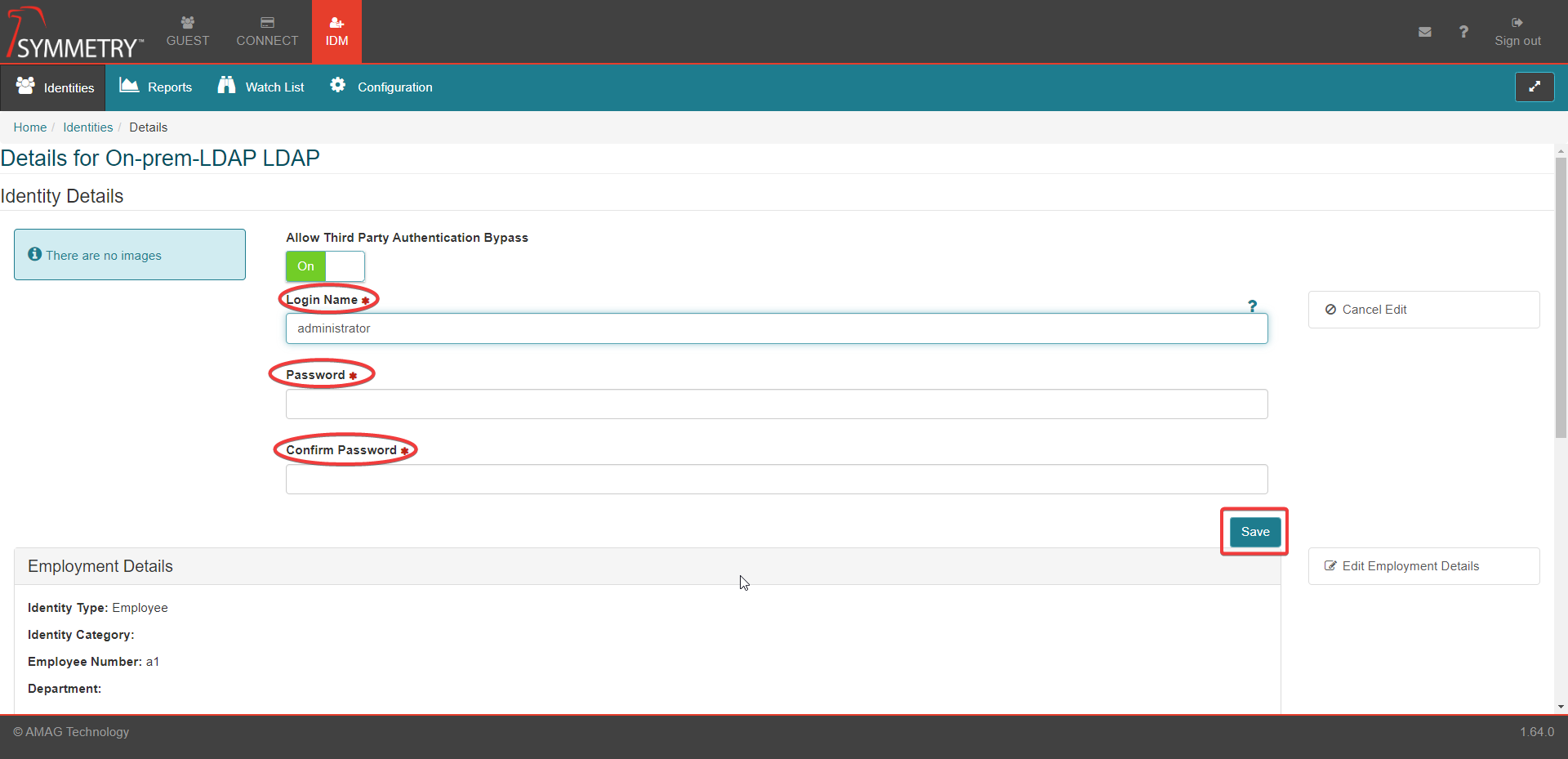
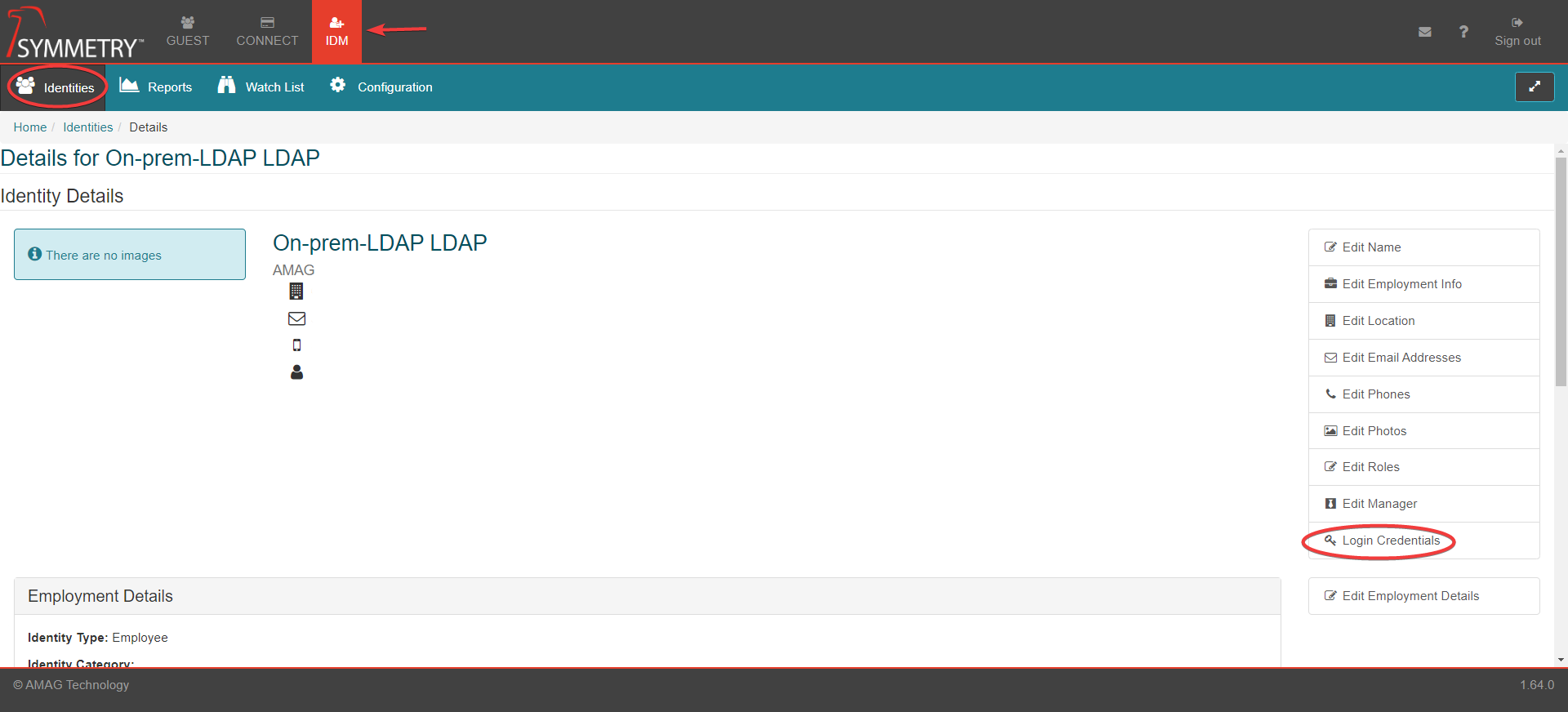
Select the IDM tab at the top of the screen.
Select the Identities tab.
Select the Login Credentials option from the menu.
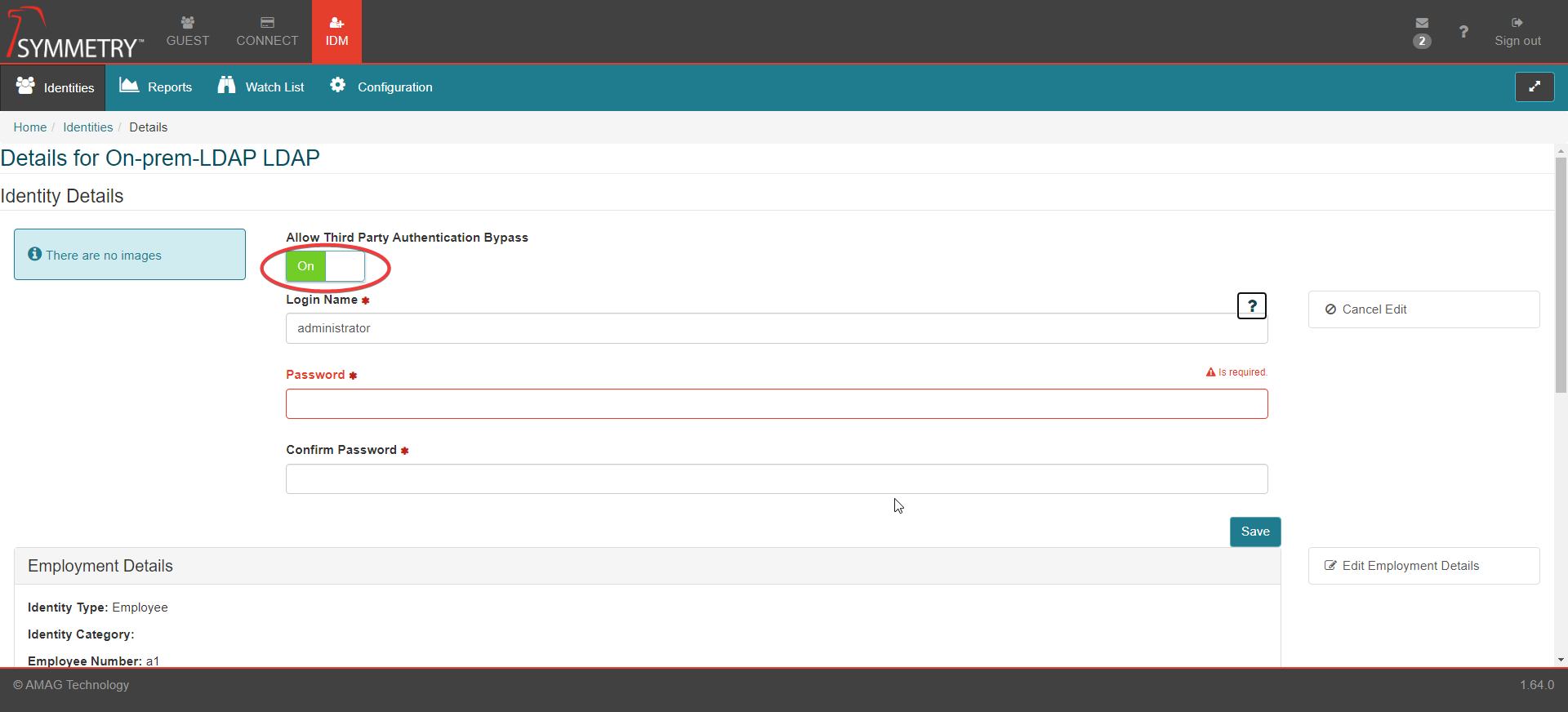
Toggle the Allow Third Party Authentication Bypass button to either On or Off as required.
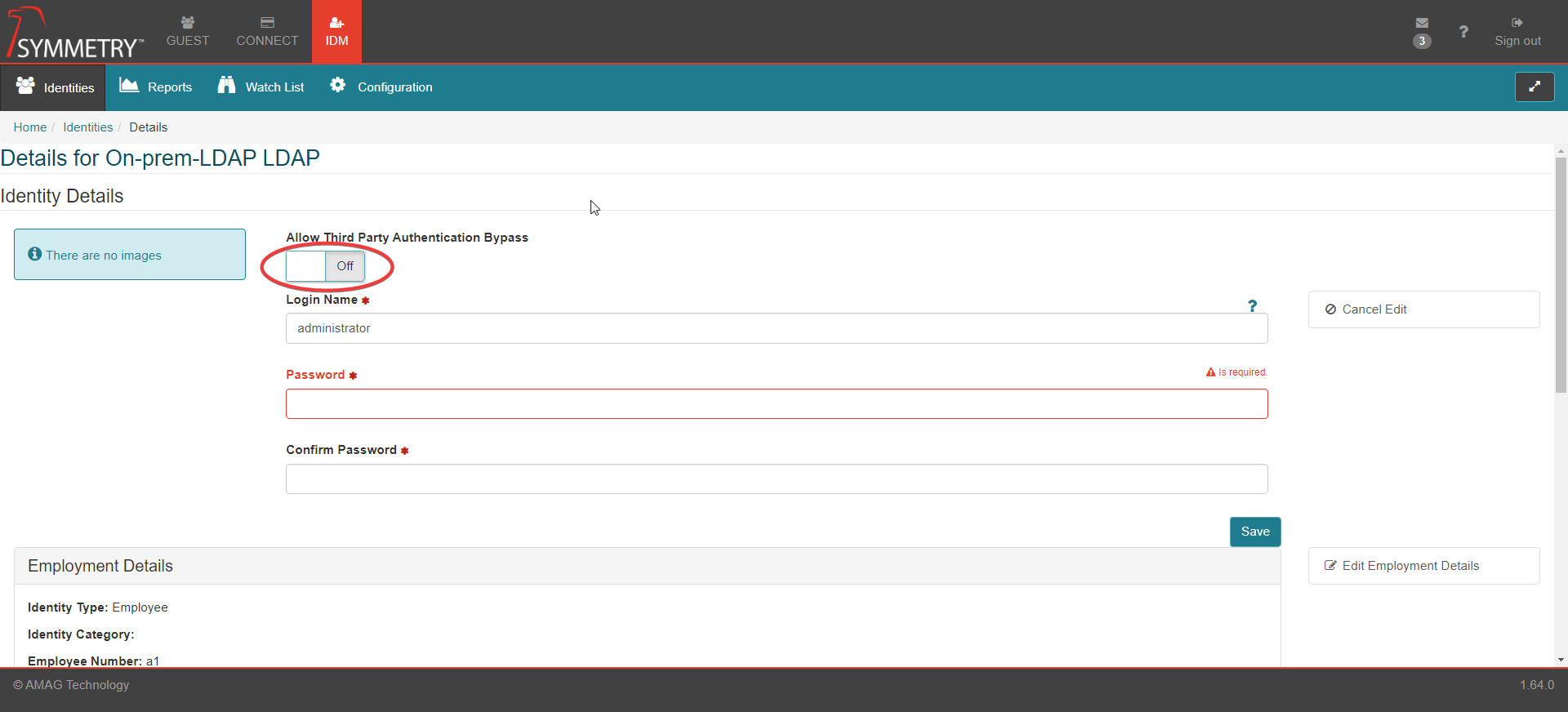
The change will be confirmed with a note (Updated Third Party Authentication Bypass) in the top right corner of the screen, as shown in the graphic below.
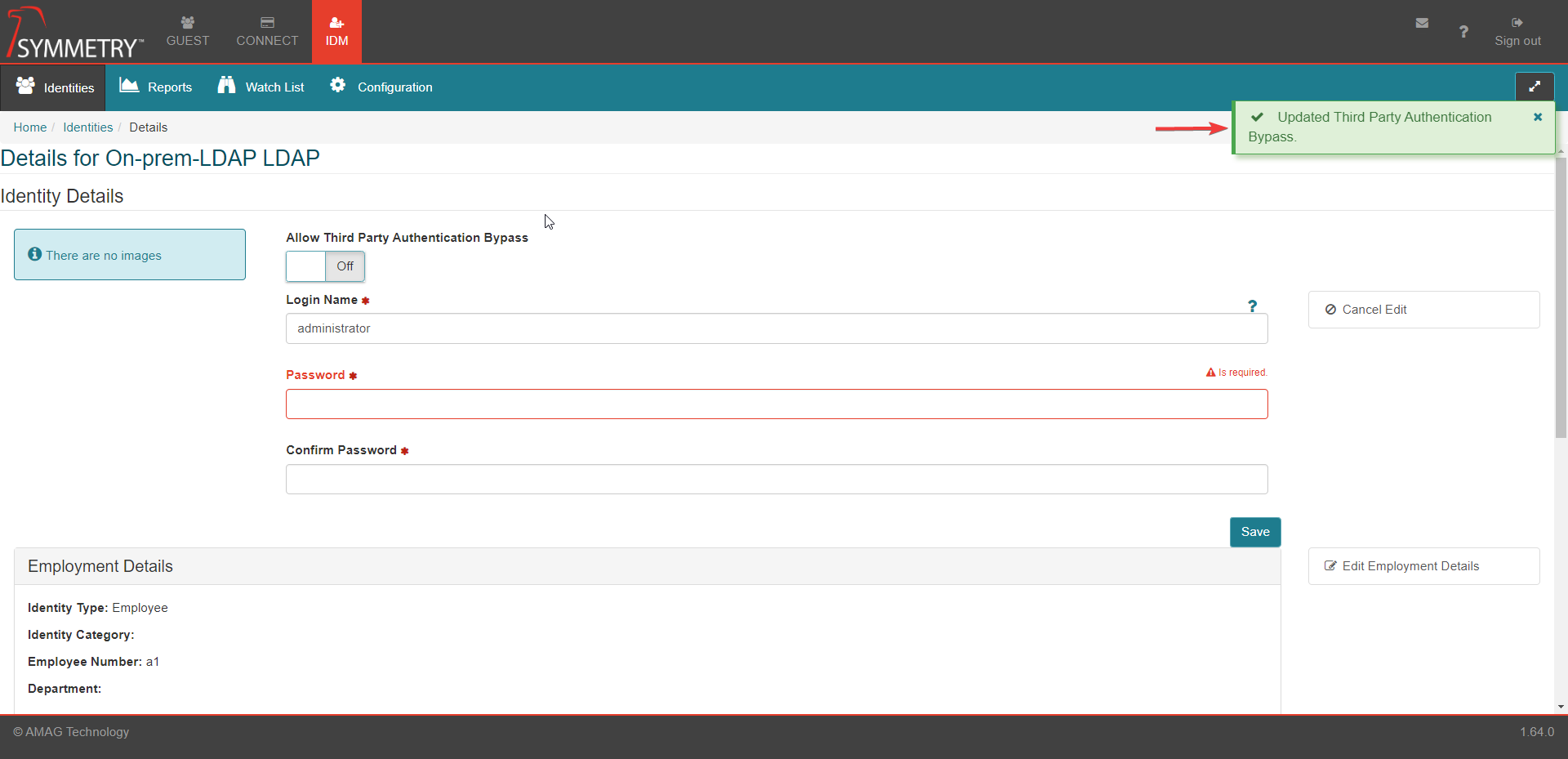
Provide user credential details to the blank fields and select the Save button.
Login Name: Users Login name
Password: Users Password
Confirm Password: Users Password (this field must match the password field)